The rise of quantum computing has drawn attention to its potential impact on Bitcoin. As this field develops, many Bitcoiners are wondering if there is a genuine reason for concern.
While quantum computing does not pose an imminent threat to Bitcoin, it’s important to know the timeframe and potential areas of impact. Bitcoin can still function in a world with powerful quantum computers, but bitcoin holders, developers, and the broader Bitcoin community must proactively address existing vulnerabilities ahead of time.
In this article, you’ll learn about the applications of quantum computing to cryptography, the potential vulnerabilities this poses to Bitcoin, and the paths ahead.
Quantum Computing and Cryptography
Quantum computing uses the principles of quantum mechanics to process information in fundamentally different ways from classical computers. While classical computers operate on bits that represent either 0 or 1, quantum computers use quantum bits, or qubits, which can exist in multiple states simultaneously due to superposition. This allows quantum computers to evaluate a vast number of possibilities at once, potentially solving certain complex problems much faster than the computers we use today.
The theoretical foundation of quantum computing was laid in the early 1980s, with physicist Richard Feynman proposing the concept of quantum simulations in 1981. The first functional quantum computer was built in 2001 by researchers at IBM and Stanford University. Since then, the field has progressed with the development of more powerful computers, but remains in a state of infancy, lacking the scale needed for practical applications.
Two Quantum Algorithms That Impact Bitcoin
Shor’s Algorithm and Bitcoin signatures
The first significant algorithm demonstrating the power of quantum computation was Shor’s algorithm, developed by Peter Shor in 1994. This algorithm showed that quantum computers could factor large numbers exponentially faster than classical methods. Bitcoin’s current signature address schemes, ECDSA and Schnorr, rely on the difficulty of factoring large prime numbers and could be impacted by Shor’s algorithm.
Grover’s Algorithm and Bitcoin mining
Grover’s algorithm, developed by Lov Grover in 1996, is another application of quantum computing relevant to cryptography. Specifically, it allows quantum computers to solve certain optimization problems in significantly less time compared to classical algorithms. This principle can also be applied to hashing, a concept integral to bitcoin mining and certain signature types.
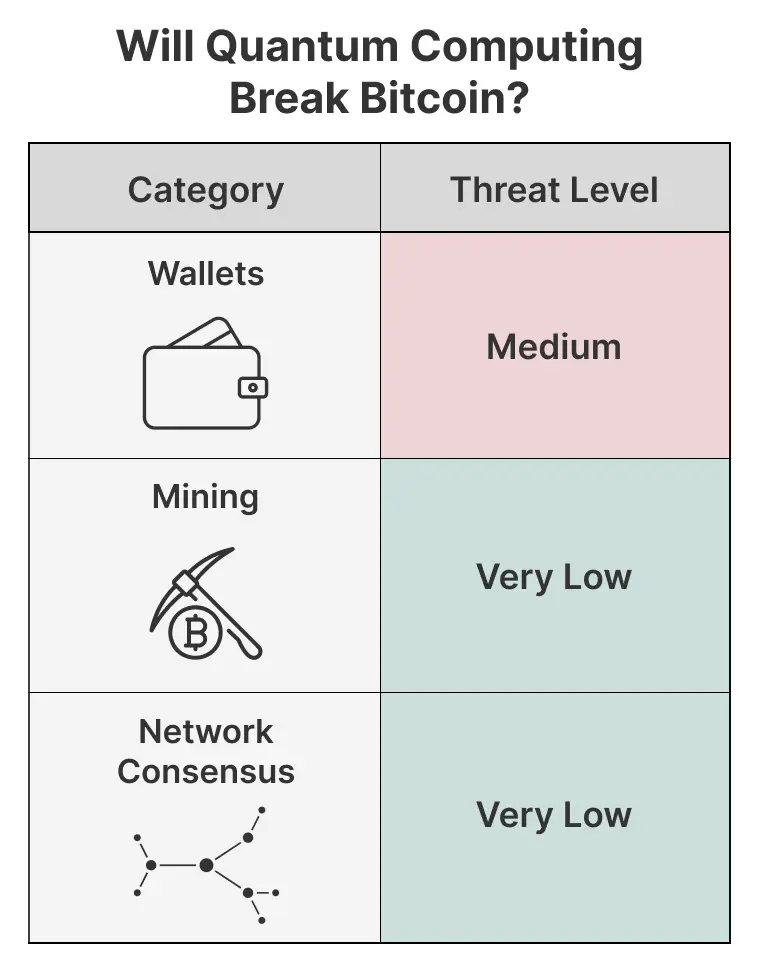
A powerful enough quantum computer using Shor’s algorithm or Grover’s algorithm poses potential threats to various aspects of Bitcoin. One primary concern is the security of Bitcoin wallets and their related addresses. However, we will also cover theoretical threats to Bitcoin mining and network consensus.
Quantum’s Impact on Bitcoin Wallets
Wallets are used to create and manage Bitcoin addresses and are the main interface for users to interact with the Bitcoin network. Bitcoin supports various address types, each with varying levels of future vulnerability to quantum computing.
When a wallet generates a public-private key pair, it relies on the mathematical properties of large prime numbers. A private key is typically a randomly generated number, which is then used in combination with functions based on prime numbers and elliptic curves to derive the corresponding public key. The difficulty of reversing these operations without knowing the private key is due to the complexity of factoring large numbers.
Quantum computing could impact Bitcoin wallets in the future by deriving private keys from public keys, and can be divided into two types of attacks: A “long range” attack affects only wallets with exposed public keys, while a “short range” attack would target all current wallet types.
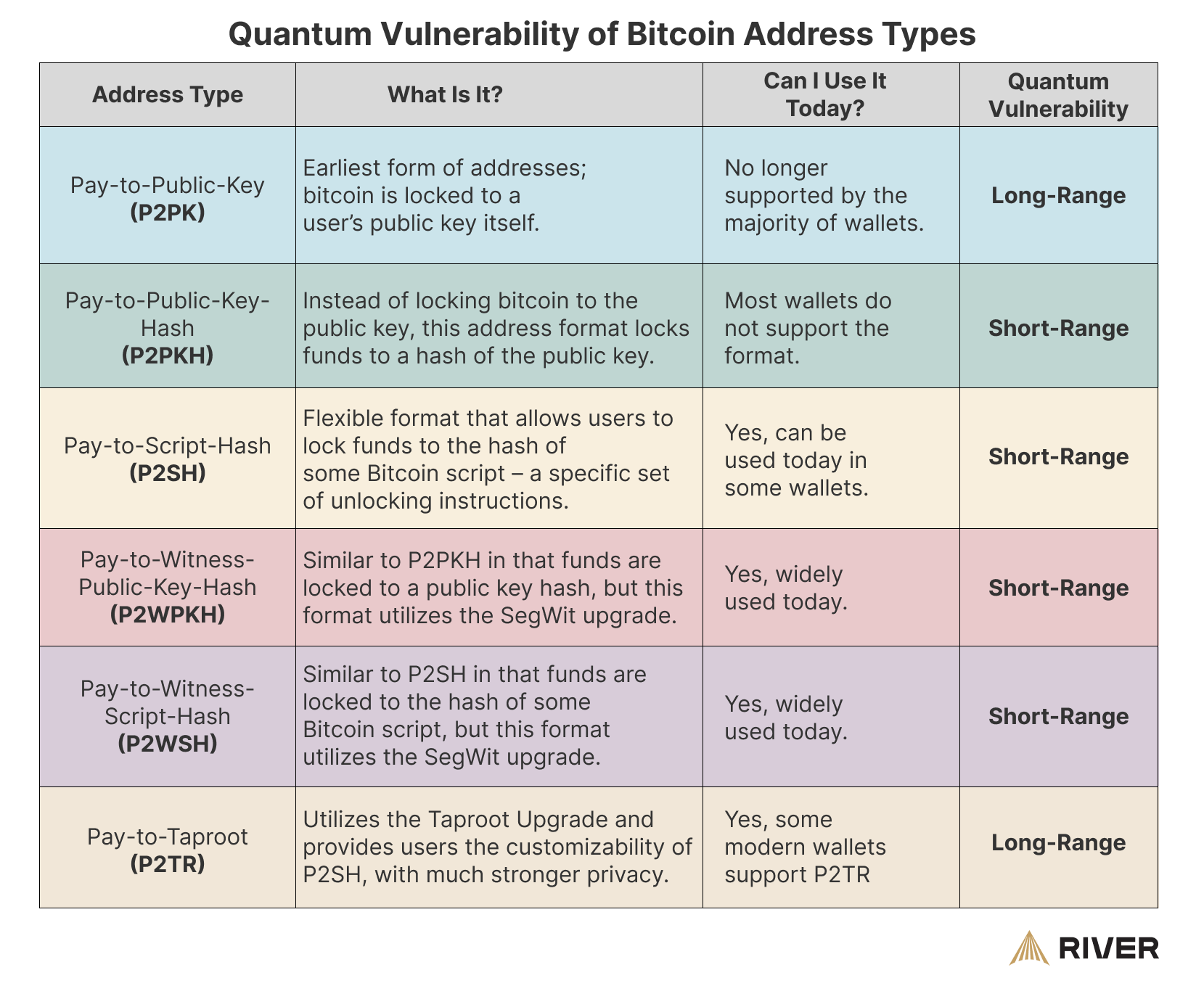
Long-Range Attacks
Any address that has exposed its public key is vulnerable to an attack by a powerful enough quantum computer. This is because a public key could be used to derive the corresponding private key using Shor’s algorithm. The chart below shows the distribution of bitcoin’s supply exposed to long-range attacks.
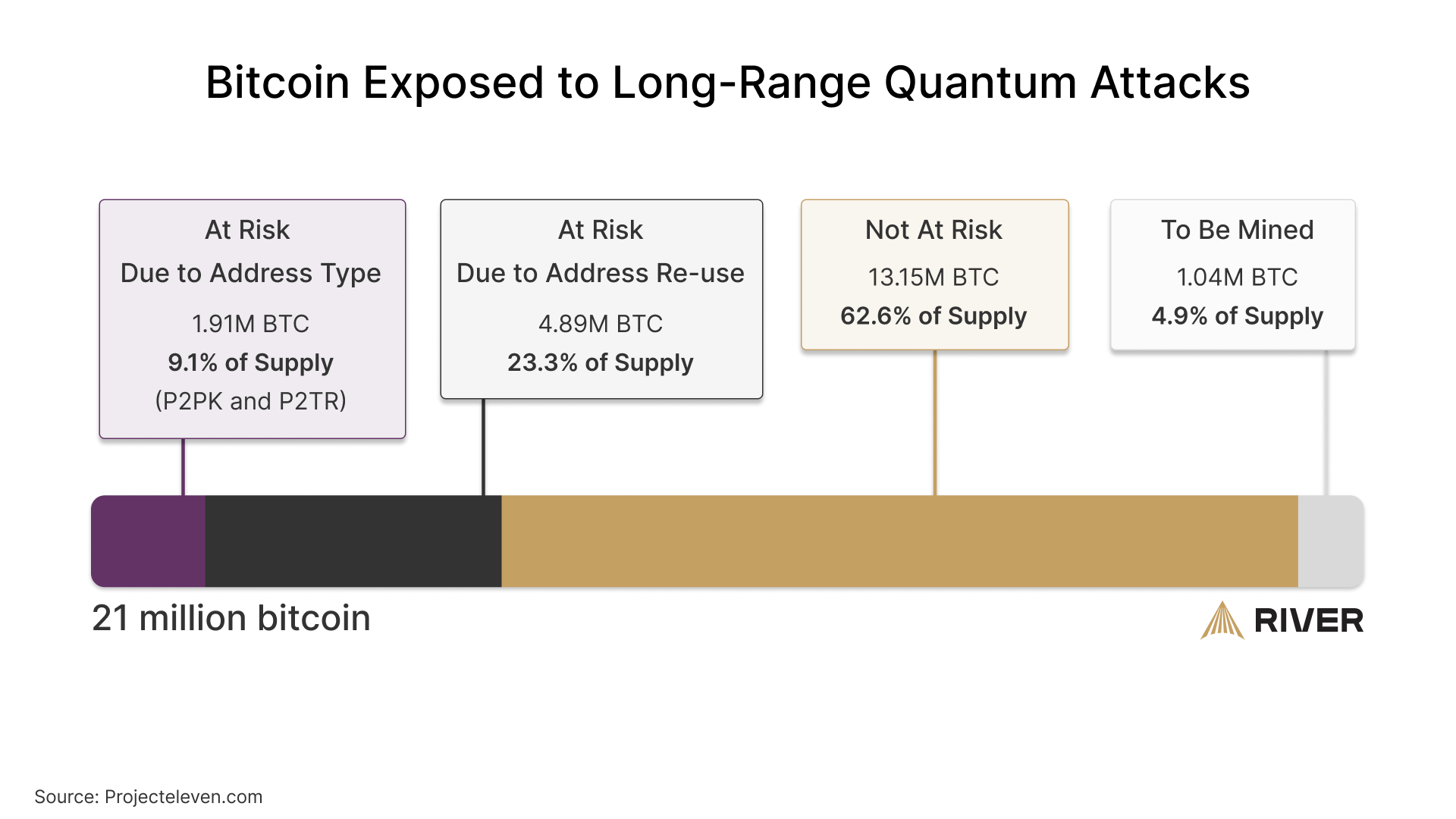
Pay-to-Public-Key (P2PK) addresses are particularly susceptible, as they use the public key directly as the address. Additionally, any address that has been reused after sending a transaction is vulnerable, because the act of transacting reveals the public key. Pay-to-Taproot (P2TR) addresses also expose the public key, but account for a small fraction of total bitcoin.
Approximately 1.72 million BTC are held in P2PK addresses, while another 4.9 million BTC are stored in reused addresses of other types. Together, this represents 6.8 million BTC potentially at risk in the future from long-range quantum attacks.
Bitcoin wallets today no longer support the P2PK address type, and typically do not reuse addresses. However, if your wallet has reused its address or uses the P2TR address type, you can protect your funds from a potential long-range quantum attack by migrating your bitcoin to a new wallet that does not reuse addresses.
To find out what address type you have, you can go to your Bitcoin wallet and find the “receive” button, which is typically displayed on the home page. A Bitcoin address will then be provided, which you can cross-reference with this River Learn article to find out what type it is. To check if your address has been reused, you can paste your address into a block explorer to see if has been used in any transactions in the past.
Short-Range Attacks
When a transaction is sent from an address, the corresponding public key is exposed in the process. This creates a temporary vulnerability lasting until the transaction is confirmed by the Bitcoin blockchain, which typically takes between 10 and 60 minutes.
A quantum computer powerful enough to perform Shor’s algorithm to derive a private key within 10-60 minutes could theoretically steal funds from any address that has sent a pending transaction. This would occur by deriving the victim’s private key and then sending a competing transaction before the victim’s transaction has been confirmed. ** ** This scenario is known as a “short-range” attack, and has potential impact on all Bitcoin wallets in use today.
Key Generation Attacks
Bitcoin addresses depend on high-quality random numbers to generate secure private keys. If the randomness used to create these keys is weak or predictable, an attacker could potentially derive the private key.
Quantum computers using Grover’s algorithm could speed up the process of exploiting weak key generation methods. While the number of addresses potentially vulnerable is unknown and likely quite low, quantum computers could potentially widen the scope of vulnerable addresses.
Quantum’s Impact on Bitcoin Mining
Bitcoin mining relies on brute-force computation using the SHA-256 hashing algorithm to discover new blocks. In theory, quantum computers using Grover’s algorithm could reduce the time required to find a new block by half, assuming equal computational power.
In practice, quantum computing does not currently pose an imminent or long-term threat to Bitcoin mining. For quantum computers to compete with the existing network of mining rigs, they would need to be produced at an enormous scale—something far beyond what is feasible in the foreseeable future. Furthermore, quantum computers require substantial energy for cooling and operation, making them highly cost-inefficient as mining devices.
Quantum’s Impact on Network Consensus
Bitcoin’s functioning relies on achieving consensus among a network of honest nodes. One potential threat to this consensus is a Sybil attack, which occurs when a network is flooded with fake nodes to disrupt transaction propagation, peer-to-peer communication, and consensus.
Quantum computers could theoretically enhance the effectiveness of Sybil attacks due to their ability to optimize complex problems, such as network analysis and evaluating multiple scenarios simultaneously. If successful, a quantum-enabled Sybil attack could block honest nodes from propagating transactions, isolate specific nodes by feeding them false blockchain data, or introduce fraudulent transactions that might be accepted as valid.
In practice, a quantum-enabled Sybil attack is unlikely to be successful even if quantum computers are able to scale rapidly. Bitcoin’s network is highly decentralized, and its consensus mechanisms are designed to discount the influence of a large influx of new, potentially malicious nodes.
When Will Quantum Computing Threaten Bitcoin?
Progress in quantum computing is often described using the number of physical qubits in a processor, and leading systems have now surpassed 1,000 physical qubits. However, raw qubit count is not a good proxy for cryptographic threat: breaking public-key cryptography requires many error-corrected logical qubits and the ability to run extremely deep circuits, which today’s machines cannot do reliably.
In 2022, researchers from the University of Sussex estimated that a quantum computer would need between 13 and 300 million qubits of processing power to crack the ECDSA signature algorithm in a reasonable timeframe of 1-8 hours.
While large-scale, fault-tolerant quantum computing remains an unsolved engineering challenge, quantum researchers have become more explicit about potential paths to fault tolerance later this decade and beyond. As a result, it’s still unlikely that quantum computers pose a practical threat to Bitcoin in the next ~10 years, but the direction of travel is clearer, and the ecosystem is increasingly discussing migration paths toward quantum-resistant outputs and signatures.
Mitigating Quantum Risks to Bitcoin
The most immediate quantum risk to Bitcoin—wallet vulnerability—has viable solutions that may be implemented in the coming years. If Bitcoiners want to protect themselves against the long-term risks of quantum computing, then it is likely that a soft fork will be required to add a quantum-resistant signature algorithm
In the short term, bitcoin held in wallets vulnerable to long-range attacks may be migrated to more secure wallets. Both solutions will require considerable time and blockspace for vulnerable funds to be moved to safe addresses.
Short-Term Solution: Wallet Migration
The roughly 6.8 million bitcoin held in P2PK and reused addresses may be migrated to address types only vulnerable to short-range attacks. Such migrations significantly delay the hypothetical time until these funds become vulnerable, as long-range quantum attacks require substantially more computational resources than short-range attacks. A full migration of P2PK outputs to safer formats like P2WSH would fill only a handful of blocks, though migrating reused addresses would take longer.
Long-Term Solution: Consensus Change to Update Signature Algorithm
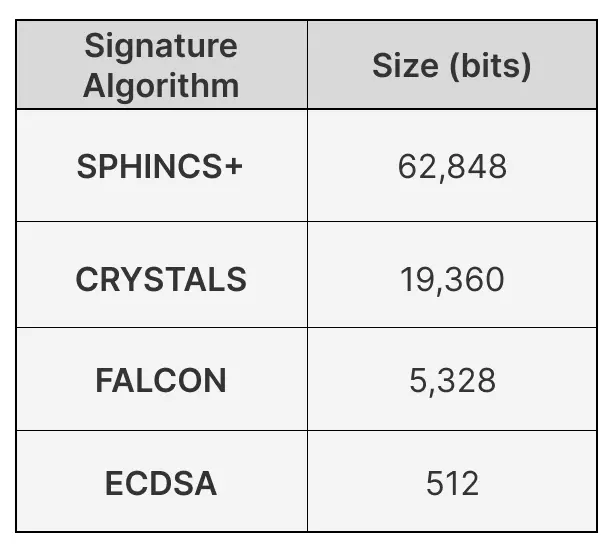
There are at least 11 existing signature algorithms that are claimed to be quantum resistant. The reliability of these post-quantum signature schemes varies widely. Notably, 8 of them were introduced after 2015 and lack the extensive testing needed to gain the trust of the developer community. Post-quantum signature schemes also vary widely in their size, an important factor given the limited blockspace available in Bitcoin blocks. Larger signature sizes could impact Bitcoin’s transaction throughput network efficiency.
The US National Institute of Standards and Technology has approved 3 of these signature schemes for use in quantum-secure encryption, meaning they have undergone sufficient testing to be seen as reliable. Compared with Bitcoin’s ECDSA signature algorithm, these post-quantum schemes are at least 10 times larger in size.
Bitcoin developers have proposed several technical approaches to make the Bitcoin protocol resilient to quantum attacks. These proposals vary in maturity, and the developer community has not yet reached consensus on a preferred direction. As of December 2025, the full set of proposals is summarized in Bitcoin Optech Newsletter #385.
The mose widely known proposal is known as BIP-360. Rather than immediately switching Bitcoin to a specific post-quantum signature, BIP-360 introduces a new address type that would render Taproot addresses immune to long-range attacks. Importantly, this change can be activated via a soft fork and does not require replacing Bitcoin’s existing signature algorithms right away.
Support for post-quantum signatures is expected to be added in a later upgrade, once specific algorithms have been tested and reviewed more thoroughly. This gradual approach mirrors what is already happening in traditional finance and technology, where systems often deploy classical and post-quantum cryptography side by side during long transition periods.
Regardless of the specific technical path chosen, all bitcoin currently held in ECDSA-based and Taproot addresses would ultimately need to be migrated to post-quantum address types to defend against short-range quantum attacks. This would require a full migration of the existing UTXO set.
An October 2024 paper by researchers at the University of Kent estimates that a full migration of vulnerable addresses would take 76 days, assuming that all Bitcoin transactions would be for migration transactions and nothing else. A more reasonable assumption, in which 25% of blockspace is used for migration transactions, suggests that a full migration would take roughly 2 years to complete.
What Will Happen to Lost Bitcoin During a Quantum Attack?
River estimates that roughly 1.6 million bitcoin are lost, in addition to Satoshi’s estimated holdings of 968,000 BTC. These coins may never be migrated to safe addresses, raising questions about what steps could be taken to potentially prevent them from being stolen through a quantum attack.
An extreme solution would involve “disabling” or otherwise moving Satoshi’s and all lost coins to prevent them from being taken by a quantum attacker. Such an action would require a soft fork of the Bitcoin protocol.
It is unlikely that consensus will be reached around this path. Disabling lost coins always runs the risk of being confiscatory, as it is impossible to prove such coins are truly “lost”. Additionally, controlling someone’s coins runs against the ideals of the Bitcoin protocol, which follows the “not your keys, not your coins” philosophy.
It is more likely that Satoshi’s coins and all lost coins will remain in their current wallets until their private keys have been forged by a quantum computer, which may never end up occurring. If this happens, it is unclear how these coins will be treated from a legal and regulatory perspective.
Key Takeaways
- A powerful enough quantum computer using Shor’s algorithm or Grover’s algorithm poses potential threats to various aspects of Bitcoin.
- Even under optimistic assumptions about the rate of advancement, it is highly unlikely that quantum computers will pose a significant threat to Bitcoin within the next decade.
- There are viable pathways to make Bitcoin resistant to quantum threats, including the QuBit soft fork.


